I’m not a super expert in all this, but I know enough to be dangerous. If I make any mistakes, please let me know (there are many ways to contact me listed in the “Contact” menu). I will clearly mark any changes to the post due to errors, feel free to check back and see what I got wrong. Since the CVE people won’t tell us anything useful, let’s use Cunningham’s Law to our advantage.
I want to try and explain where we are a week after CVEmageddon and set some expectations for what happens next. I’ll spare you a TL;DR recap, there are many stories about it already.
The contract
So let’s start with the CVE funding. There is a website, USAspending, that has the CVE funding contract details. In that contract, there is this image
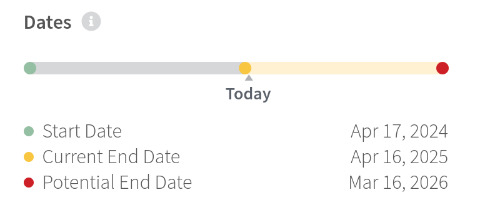
You can see we’re now in the yellow portion of this image. So what happened with the CVE contract? The short summary is nothing happened, there’s no new contract, we’re still operating under the rules of the old contract. If we look at the data on USAspending, we can see a line that says
P00006 | 04/16/2025 | $3,983,116 | G: EXERCISE AN OPTION | EXERCISE OPTION PERIOD 1. 2(D).
That’s the money that is keeping CVE alive. About four million dollars. Is that enough to keep CVE alive for a year? I have no idea. We have been told there is enough funding for 11 months.
But that 11 month number lines up with the date in that image, March 16 2026. The contract expires on that date. Is four million dollars enough to run CVE for 11 months, or is it enough to run CVE for less than 11 months? If the CVE money runs out before March 16, and there isn’t another option extension, CVE goes away.
Update: CISA has released a statement about this debacle. Nothing above changes based on that statement. We need to see a new contract from CISA before the above is invalidated.
MITRE
So that brings us to the next question I hear, which is why doesn’t MITRE just pay for CVE? It’s because they can’t, well, not legally.
This part is a little complicated, I’ll try to keep it easy. When we say MITRE, we really mean an organization called “The Mitre Corporation” which is a 501(c)3 not-for-profit corporation in the US. Inside MITRE, there are things called FFRDCs or Federally Funded Research and Development Centers. The FFRDC is what actually runs the CVE program. It should come as no surprise that an FFRDC is heavily regulated. All of the work they do has to legally be tied to a federal contract and the money spent in very specific ways. They can’t just decide they’re going to change what they’re spending money on.
So, putting all these pieces together, MITRE can’t legally pay to keep the lights on at the CVE program. When the funding is gone, that’s it, CVE is done. This brings us to that contract. We’re in what’s now called the option period. It’s common for federal contracts to have option periods at the end. Historically I’ve seen these use to cover funding gaps, like when a US budget is a few months late, someone is on vacation, the lawyers are really slow, stuff like that. The options aren’t meant to fund something in place of a proper contract. But more importantly, the option runs out on March 16 2026. Unless there is a new contract, there’s no way to pay for CVE to exist after the March 16 date.
We have no idea if anyone is trying to get a new contract in place before March 16.
The CVE Foundation
And lastly, let’s cover the CVE foundation. I did give them a comically low score in my last blog post Can we trust CVE? I want to cover this group because the name has led many people to assume the CVE Foundation is the CVE program creating somewhere for CVE to live in the future.
We still don’t know if this foundation is endorsed or approved of by the CVE program, CISA, or MITRE. I asked this bluntly to one of their board members, they wouldn’t answer the question, which likely means it is not.
This is also a pretty clear trademark violation, MITRE holds the trademark for CVE. It’s possible that trademark wouldn’t stand up in court, or MITRE never enforces it, but the idea behind a trademark is to avoid situations where one group misuses the mark and creates confusion, a bit like this.
When I wrote my last post there was no real details on the CVE Foundation site. Now they have a FAQ. Interpreting it is an exercise for the reader.
Help make this post better
I’m quite certain I got some of the details wrong. I would appreciate a note with any details for corrections. I’m happy to take them anonymously and I’m just as happy to credit you in the edit.
If this is a topic you’re interested in, there’s a discord chocked full of people discussing vulnerability things, feel free to join
